We will help you set up a great employee portal.
Discover the security solutions to help you put security everywhere
Our broad cybersecurity knowledge and deep industry expertise allow us to develop next-gen cybersecurity services to protect your business, from end to end.
Enterprise Web Apps
We perform web application security testing to check if essential security controls are reliable, security features are configured correctly, and ongoing security monitoring is in place.
Mobile Apps
Our security teams stick to best practices in mobile security to help companies set up end-to-end defense of their corporate and customer-facing mobile apps across all platforms.
Cloud Apps
With mature skills in cloud computing, we discover and eliminate cloud security risks to help our clients feel as secure in the cloud as they would with on-premises systems.
Embedded Software
Our services cover embedded firmware analysis and testing. We work to prevent security flaws in stand-alone and connected devices to guarantee their operational and data safety.
How to out-innovate cyber attackers
Our security expertise includes a variety of testing techniques to address all possible testing areas and help organizations with their targeted security activities.
Vulnerability Assessment
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Security Audit
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Penetration Testing
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Compliance Testing
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Security Code Review
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
Security Stress Testing
We assess your technological maturity and readiness for AI-driven automation and follow you through all the stages of adopting artificial intelligence in your business operations, from analyzing your use case to developing AI-driven software and ensuring its positive user buy-in.
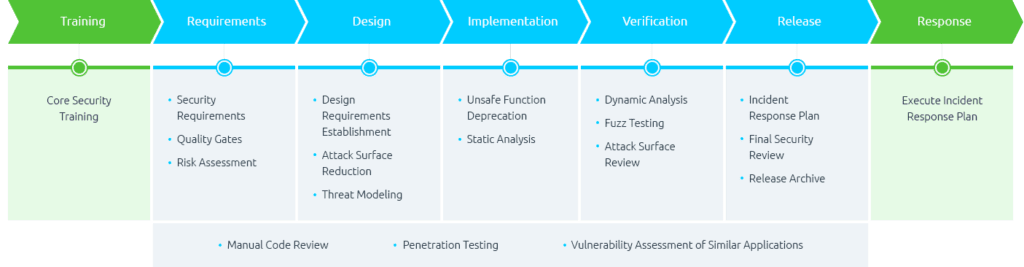
WE put security everywhere
We Protect your business with a security strategy defined by zero trust. We build security pillars at all levels, helping organizations minimize the risk of security incidents throughout the SDLC and release cyber-immune solutions.
We will help you set up a great employee portal.
Test Your Users and Your Network
Dynamic application security testing (DAST)
While applying this black-box testing technique, our certified ethical hackers try to compromise a running web app from the outside. By simulating the most popular cyber attacks, we check how reliable and ready a web app is to hold out against a real intrusion.
Static application security testing (SAST)
We perform SAST concurrently with app development to verify the solution contains no flaws and can be deployed securely. This white-box testing method helps release healthy and protected web apps along with reducing the investment into post-deployment testing.
Client-side app security testing
Trying to execute attacks on the client-side of a web app, we reveal how susceptible the app is to commonplace attacks, including XSS, HTML injections, CORS, clickjacking, etc. We assess the severity of detected vulnerabilities and their potential impact in case of a successful penetration.
Server-side app security testing
Our services cover embedded firmware analysis and testing. We work to prevent security flaws in stand-alone and connected devices to guarantee their operational and data safety.
TOP SOFTWARE SECURITY CONSULTING
When organizations need to go beyond typical security checkups, datawalls comes with extended security services. We’ll base them around your needs to build a solid security ground for all current and to-be-deployed software, to restore a secure digital environment, or add to your running security activities.
Security Planning
We help companies embark on their software security with a long-term security roadmap. We create a unique guide to security measures based on organizational infrastructure, deployed and planned software, as well as financial capabilities.
Security Recovery
When a company experiences an attack or struggles with security issues regularly, datawalls comes with remediation scenarios. We patch affected solutions and apply security measures to prevent more breaches and stamp out security threats.
Security Enhancement
We assist organizations in need of advanced security. We improve existing security controls, as well as select and implement new features and tools for ongoing protection and 360-degree monitoring of internal and customer-facing solutions.
OUR DELIVERABLES: YOUR FIRST STEP TO IMPROVED SOFTWARE SECURITY
At all levels of application security consulting, we provide our clients with tangible deliverables for them to take optimal security steps.
Detailed Security Testing Report
We finalize our security testing with an all-inclusive report that sums up performed activities and detected security issues sorted by their severity, cause, and nature.
Ready-to-Apply Security Measures
Our security engineers compile a list of countermeasures to eliminate revealed security flaws. We can also provide experts to implement these security recommendations.
Short- and Long-Term Security Strategy
As part of software security consulting, we come up with a comprehensive security strategy that covers every aspect of software security management at your enterprise.
WANT TO START A PROJECT?
It’s simple!
By submitting this form i give my consent for Datawalls to process my personal data
pursuant to Datawalls privacy and Cookies Policy.

